2 Identity theft has swiftly become a serious issue for victims police and prosecutors and is a. Ad Best Identity Theft Protection Services 2022.

Pdf Online Id Theft Techniques Investigation And Response
All Major Categories Covered.

. Seeking Victims in Identity Theft Investigation. Identity theft occurs when someone uses your identity in a crime or fraudulent act. As technology advances so do the techniques used by identity thieves.
Ad A Free Online Course On Protecting Yourself From Identity Theft. Ad Answer Simple Questions to Make An ID Theft Affidavit On Any Device In Minutes. Examples of how stolen personal information can be used to.
Easily Customize Your ID Theft Affidavit. Identity Theft happens to 1 Out of 4. Other types of identity theft.
Ad Have Full Control of Your Credit Activity. Identity Theft happens to 1 Out of 4. Join a Plan Today Starting 899.
Proof of your address mortgage statement rental agreement or utilities bill Any other proof you have of the theftbills Internal Revenue. Dont Be That One. Dont Be That One.
For example training in identity theft usually involves providing investigators with the newest investigative techniques resources and victim-related issues. The University of Glamorgan and is currently working towards a PhD in Data. This paper presents an evaluation of the.
Mining of Intrusion Detection Systems. The ID Theft investigation framework disti nguishes the examination in the victims and the. A government-issued ID with a photo.
Fraudsters use a variety of techniques to acquire a victims card number. Empower Yourself And Your Career With Thousands Of Free Accredited Courses. The state with the highest per capita rate of.
Identity theft since it may occur only once and be discovered quickly by the credit card issuing company often before even the individual card holder knows it. With the growth of technology protecting your personal information has never been more important. However these have some limitations in the m-commerce.
Be Safe from Fraudulent Transactions Loans. The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and. Download Print Anytime.
Online ID theft techniques investigation and response 77. Get Protection from Identity Theft. E xamining identity theft suspects requires systematic methodical techniques designed to yield evidence for possible prosecution.
Online ID theft techniques investigation and response 77. See our ID Protection Reviews Find Who Is Rated 1. Online organisations commonly use electronic commerce approaches.
Fraudsters side and the first level of this investigati on process analysis was hence presented. Compare Identity Theft Protection Reviews. The threat of identity theft is on the rise.
It can happen to anyonebut there are steps you can take to protect yourself and to recover if it happens to. Join a Plan Today Starting 899. Be Safe from Fraudulent Transactions Loans.
If an identity theft suspect has been arrested request. Ad Have Full Control of Your Credit Activity. These techniques are listed under three headings.
And 3 social engineering. Topics within identity theft. The number of people affected by identity theft grew by 500000 people from 126 million in 2012 to 131 in 2013 with escalating losses as well.

Identity Theft Investigations Pinow Com

Identity Theft Investigations Insight Investigations

Calameo Identity Theft Protect Your Identity Online
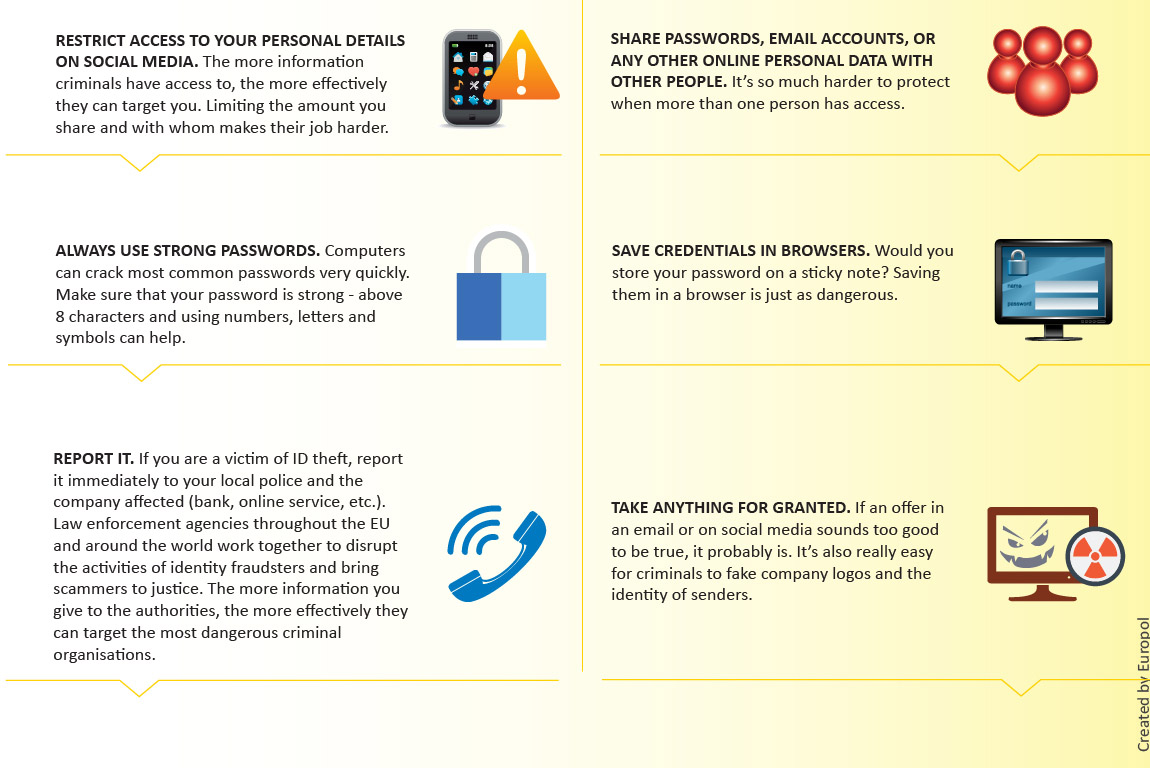
Tips And Advice To Prevent Identity Theft Happening To You Europol

Tips And Advice To Prevent Identity Theft Happening To You Europol

0 comments
Post a Comment